How to Integrate Physical and Digital Security in 5 Steps (Easy Guide for Security Leaders)
CS
Gone are the days when physical security and cybersecurity operated in separate silos. Modern threats don't respect those boundaries, and neither should your security strategy. If someone can tailgate into your building and plug a USB into a workstation, your million-dollar firewall just became useless.
The good news? Integrating physical and digital security isn't rocket science. It just requires a systematic approach and the right mindset. Let's walk through the five steps that'll get you there.
Step 1: Conduct a Comprehensive Security Assessment
Before you can integrate anything, you need to know what you're working with. This isn't about checking boxes on a compliance form—it's about understanding your real-world vulnerabilities.
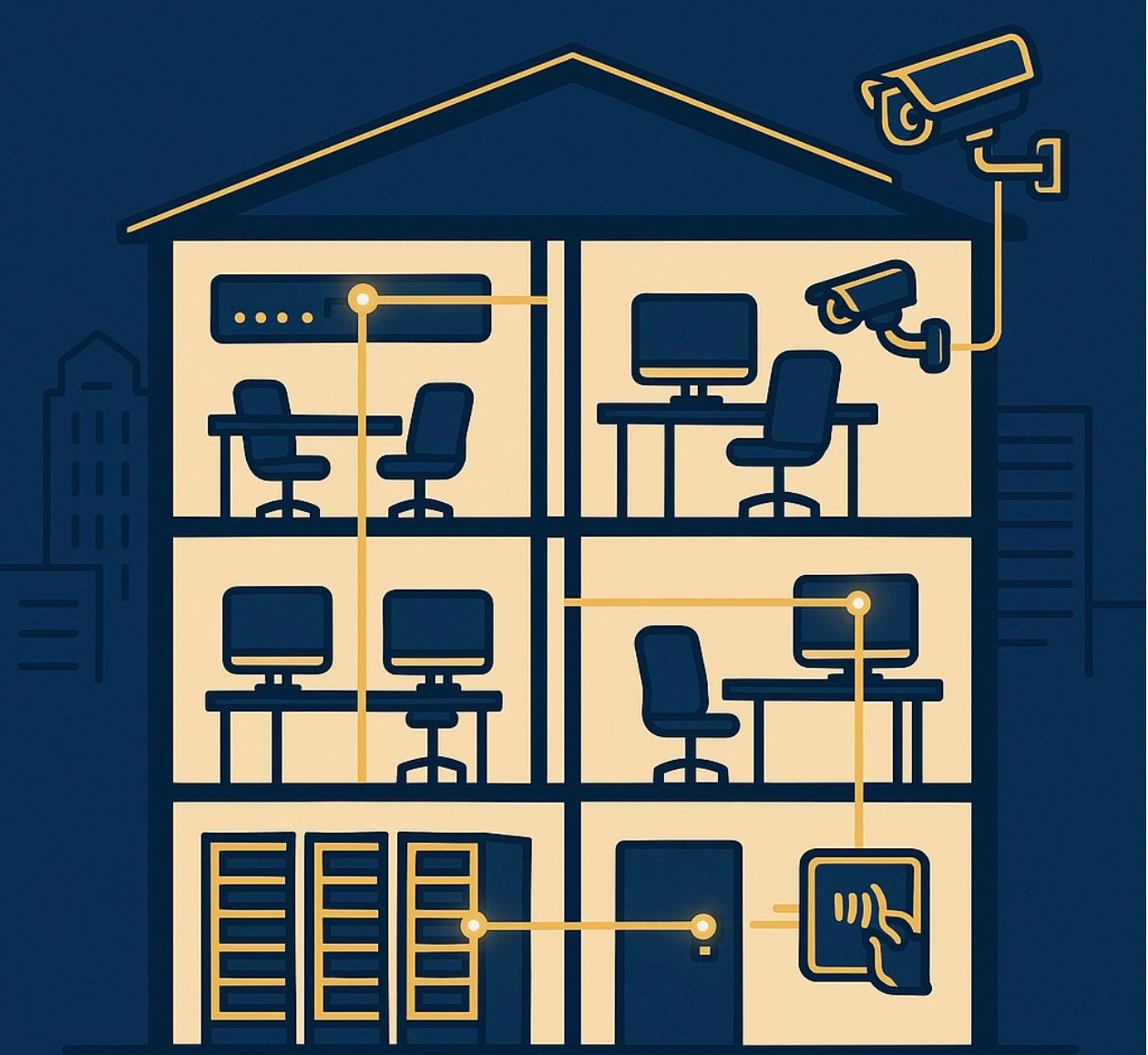
Start by mapping out all your physical assets: buildings, access points, surveillance systems, and security devices. Then do the same for your digital infrastructure: networks, servers, endpoints, and data flows. The magic happens when you identify where these two worlds intersect.
Look for critical connection points like:
-Server rooms with physical access controls
-Network equipment in unsecured locations
-IoT devices that bridge physical and digital domains
-HVAC systems with network connectivity
-Badge readers connected to your IT network
Don't forget to assess your human element. Your employees are often the bridge between physical and digital security—sometimes in ways they don't even realize. That helpful person who holds the door open for someone without a badge? They just bypassed your access control system and potentially gave a threat actor direct access to your network.
This assessment phase should reveal gaps in both domains and, more importantly, show you where those gaps create compound risks. A missing security camera becomes a bigger problem when it's covering the area where your wireless access points are installed.
Step 2: Align Stakeholders and Break Down Silos
Here's where things get interesting—and where most integration efforts fail. Your IT team thinks the physical security folks are stuck in the stone age. Your physical security team thinks IT overcomplicated everything. Meanwhile, facilities management wonders why they weren't invited to the meeting.
Create a convergence team that includes representatives from all relevant departments: IT, physical security, facilities, legal, HR, and senior leadership. This isn't a committee—it's a working group with real decision-making authority.
Define clear roles and responsibilities upfront. Who owns what when a security incident spans both domains? If someone uses a stolen badge to access a server room and install malware, is that a physical security incident or a cyber incident? (Hint: it's both, and your response needs to reflect that.)
Get executive buy-in early and often. Security convergence requires investment in technology, training, and process changes. Without leadership support, you'll find yourself fighting for resources while trying to coordinate between departments that have competing priorities.
Consider bringing in external expertise to facilitate this process. A Virtual CSO can provide the neutral perspective and specialized knowledge needed to navigate organizational politics while building an effective integrated strategy.
Step 3: Design Your Integrated Technology Architecture
Now for the fun part—actually connecting your systems. But before you start buying new gadgets, remember that integration is about making your existing investments work better together.
Start with your access control system. Modern access control platforms can serve as the foundation for broader security integration, connecting to video management systems, intrusion detection, visitor management, and even IT systems for automated account provisioning and deprovisioning.
Your video surveillance system should integrate with access control to provide visual verification of events. When someone badges in after hours, you want to automatically pull up the relevant camera feeds and verify that the person using the card is actually the cardholder.
Network segmentation becomes crucial when you're connecting physical security devices to your IT infrastructure. Create separate VLANs for security systems, implement proper firewall rules, and ensure that a compromised camera can't become a gateway into your corporate network.
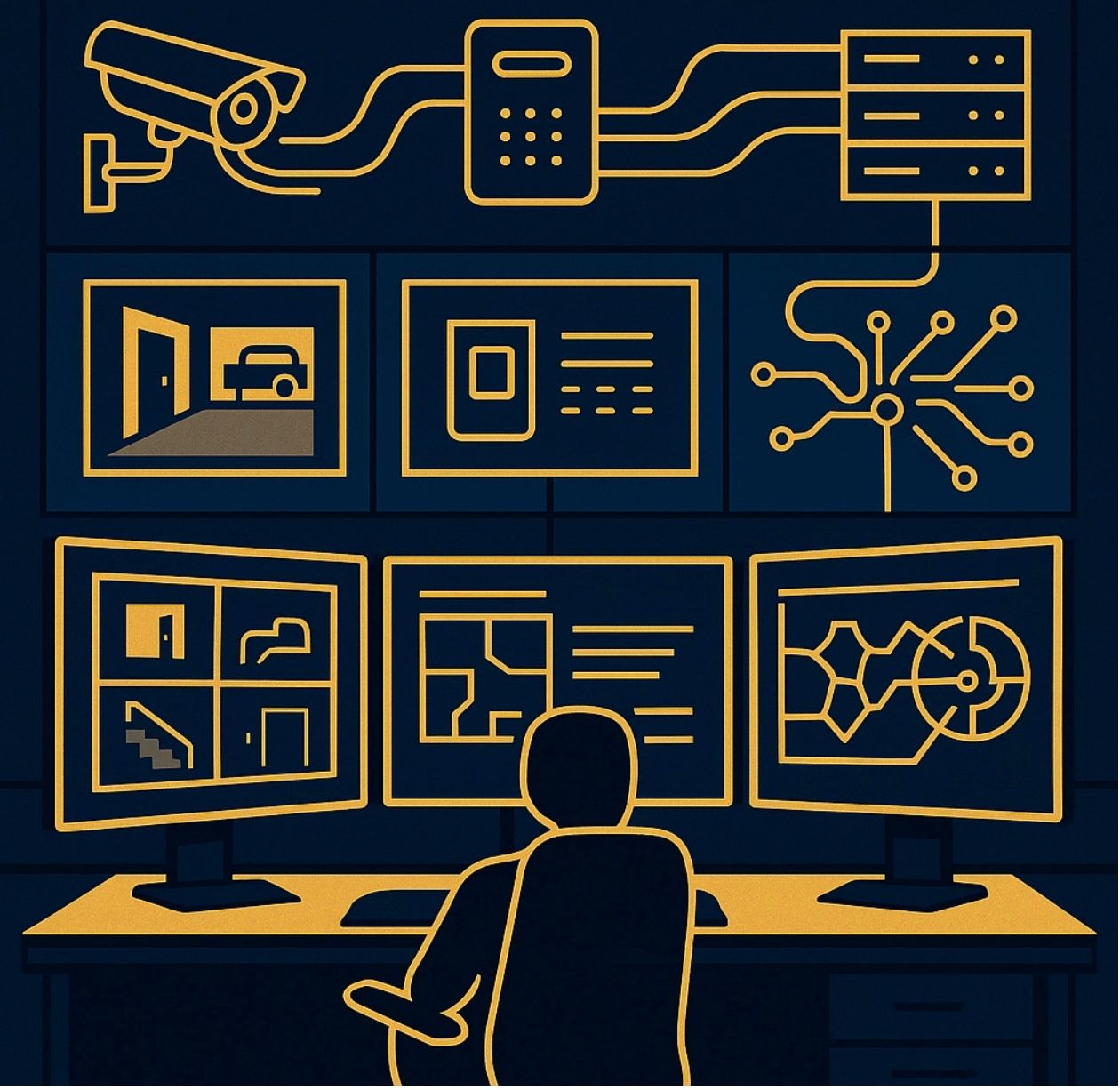
Consider cloud-based security platforms that can unify management across multiple systems and locations. These platforms often provide better integration capabilities than trying to connect disparate on-premises systems from different vendors.
Don't forget about mobile integration. Your security team should be able to receive alerts, view camera feeds, and manage access permissions from their smartphones. When physical and digital security events happen simultaneously, response time is critical.
Step 4: Develop Integrated Policies and Procedures
Technology integration without process integration is like having a sports car with square wheels—it looks impressive but doesn't actually get you anywhere.
Your incident response procedures need to account for scenarios that span both physical and digital domains. When you detect unusual network activity from a specific location, your procedure should include checking physical access logs and camera footage for that area.
Create joint training programs that help your IT staff understand physical security concepts and your physical security team grasp cybersecurity fundamentals. Everyone doesn't need to become an expert in both domains, but they need enough knowledge to recognize when an incident in their area might have implications for the other side.
Update your vendor management processes to ensure that physical security vendors meet the same cybersecurity standards as your IT vendors. That new camera system might have great image quality, but if it's running outdated firmware with known vulnerabilities, you've just created a new attack vector.

Develop clear escalation procedures that define when and how to engage both physical and digital security resources. A data center intrusion should immediately trigger both physical response (guard dispatch, area lockdown) and cyber response (network monitoring, system access review).
For organizations that don't have the internal expertise to develop these integrated procedures, working with a security consulting firm that understands both domains can accelerate the process and ensure nothing falls through the cracks.
Step 5: Monitor, Measure, and Optimize
Integration is not a one-time project—it's an ongoing process that requires continuous attention and refinement.
Implement unified dashboards that provide visibility into both physical and digital security metrics. Your security operations center should be able to see badge access events alongside network security alerts, creating a complete picture of your security posture.
Establish key performance indicators (KPIs) that measure the effectiveness of your integrated approach. Track metrics like:
-Mean time to detection for incidents spanning both domains
-False positive rates for correlated alerts
-User satisfaction with integrated security processes
-Cost savings from consolidated vendor relationships
Regular testing is essential. Conduct tabletop exercises that simulate scenarios requiring coordinated physical and digital response. Test your technology integrations to ensure data flows properly between systems and alerts trigger appropriate actions.
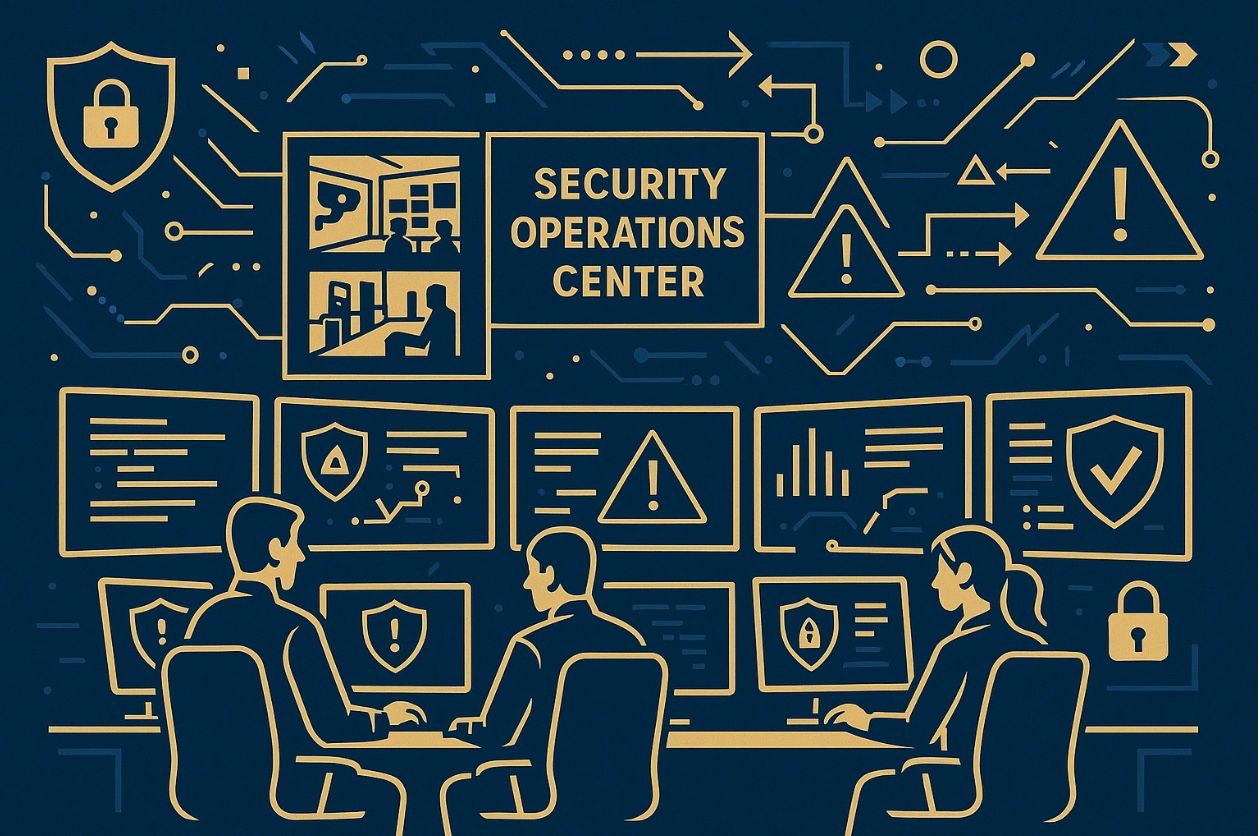
Stay current with emerging threats that target the intersection of physical and digital security. Attend industry conferences, participate in information sharing groups, and maintain relationships with law enforcement and other security professionals.
Consider quarterly reviews of your integrated security program with all stakeholders. Technology changes, threats evolve, and organizational needs shift. Your security integration strategy needs to adapt accordingly.
Making It Work in the Real World
Integrating physical and digital security sounds complex, but it doesn't have to be overwhelming. Start small, focus on high-impact connections, and build momentum through early successes.
Remember that perfect integration isn't the goal—effective integration is. You don't need every system talking to every other system. You need the right systems sharing the right information at the right time to enable better security decisions.
The organizations that succeed with security convergence treat it as a strategic initiative, not a technical project. They invest in people as much as technology, and they maintain focus on outcomes rather than getting lost in the complexity of implementation.
Ready to start your integration journey but not sure where to begin? The security experts at Civic-Shield have helped organizations across various industries successfully converge their physical and digital security programs. Whether you need a comprehensive assessment, strategic planning support, or ongoing Virtual CSO services, we can help you build an integrated security approach that actually works.
Don't let another day pass with security silos that create unnecessary risk. Your threats aren't waiting—and neither should your response to them.
